How America Loses the Next War (Part V of V)
If information war shapes the battlefield, then the trolls are combatants.
Welcome to the final installment of my series, "How America Loses the Next War." As I prepare to present this critical information at the Texas Cyber Summit on September 28th, I invite you to join my journey by subscribing to my Substack. Your support enables me to delve deeper into these pressing topics that are now my full-time focus.
For those who'd like to explore the presentation slides, they are available at the conclusion of this article. If you're part of the military or law enforcement and wish to utilize my slide deck for your presentations, please don't hesitate to contact me; I'll gladly provide you with the necessary materials.
Consider gifting a subscription to someone who might find value in the insights shared on this Substack. Your support helps spread awareness and understanding of these critical issues.
To provide context, here's a brief recap of the previous parts in this series:
Part 1 - DEVOPS
Information Warfare Shapes the Battlefield
Shaping the battlefield is the process of setting up the environment that you want in order to win.
Private companies create shaping operations to position their product by strategically influencing the market and consumer perceptions through targeted marketing campaigns. When Hoda Kotb and Kathie Lee Gifford appear on the
”Today Show” with Burger King fries, the objective is to shape the fast food battlespace.
In military operations, shaping the battlespace involves actions to control key terrain, disrupt enemy plans, or build favorable conditions for future engagements. Ukraine’s efforts to attack the Kerch Strait Bridge are shaping operations designed to influence the battlespace in Crimea and southern Ukraine.

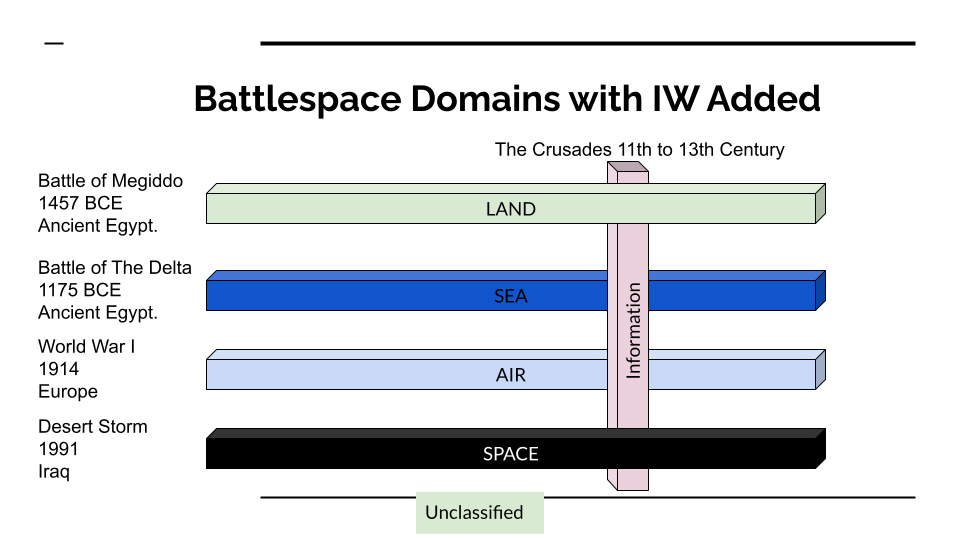
The Evolution of the Battlespace
Land and Sea were the battlespace for most of human existence.

Air power became a battlespace in 1914.

It can also be argued that Space became a battlespace in 1991 when GPS was used to guide coalition troops during Operation Desert Storm. Today, space often intertwines with the "air" domain.

The Rise of Information Warfare
The first instance of Information Warfare could be considered The Christian Crusades against the Muslim occupation of Jerusalem during the 11th to 13th centuries. While it doesn’t fit the traditional definition of Information Warfare, The Catholic Church, particularly the Pope, played a significant role in promoting the Crusades. Papal bulls and proclamations were issued to rally Christians to join the holy cause, promising spiritual rewards for those who participated. These messages were disseminated throughout Europe to encourage recruitment.
A more recent instance of Information Warfare would be the novel Uncle Tom’s Cabin by slavery abolitionist Harriet Beecher Stowe. Uncle Tom's Cabin is believed to have significantly influenced perceptions of African Americans and the institution of slavery in the United States, with many attributing it to having played a pivotal role in setting the stage for the American Civil War.
The first instance of modern information warfare came in 1915 during World War I after the sinking of the RMS Lusitania, a British passenger liner, by a German submarine. The Germans had recently declared “unrestricted warfare” against British shipping, meaning that any ship would be destroyed onsite as opposed to stopped, boarded and searched for war material.

Britain used the incident to turn world opinion against Germany.
Germany used the incident to justify its war.

128 of the casualties on the liner were American citizens.
America used the incident to justify its entrance into the war in 1917.
The modern equivalent of a propaganda poster is the internet meme. Some of the Anti-Ukraine/ Pro-Russian memes are cleverly constructed, and designed to justify the war or raise the specter of nuclear conflict.








So now the battlespace looks like this, with Information warfare weaving its way through all domains.
Cyberattacks as Warfare
Cyberattacks have become a recognized form of warfare. The first cyberattack is widely considered to be Stuxnet. This was a highly sophisticated cyber operation discovered in 2010, believed to have been jointly developed by the United States and Israel. It specifically targeted Iran's nuclear program by sabotaging industrial control systems, damaging centrifuges used for uranium enrichment, and setting back Iran's nuclear ambitions.
But the first true Cyberattack could be considered the Estonian Cyberattack of 2007. The Estonian cyberattack of 2007 was a series of coordinated cyberattacks primarily involving distributed denial of service (DDoS) attacks that targeted Estonia's digital infrastructure, including government websites, media outlets, and financial institutions. These attacks occurred in the context of political tensions between Estonia and Russia following the relocation of a Soviet-era war memorial in Tallinn, Estonia's capital. While the attackers were not definitively linked to the Russian government, the incident raised concerns about the use of cyber operations for political purposes and highlighted vulnerabilities in critical digital infrastructure.
So now we need need to add cyberwarfare to the graphic of battlespaces.
How to Fight in the Multidimensional Battlespace
We know how to fight in the traditional domains of Land, Sea, Air / Space. The Fighting in the Cyber domain is relatively new, but tends to be constrained to using offensive and defenses cyber techniques.
No plan exists for fighting in the Information domain and this is a huge problem.
The information domain presents unique challenges. We lack a comprehensive strategy for fighting in this crucial space, even though information can shape the battlefield just as effectively as physical actions. The information domain can be used to shape the battlefield no differently than destroying a bridge shapes the land domain or establishing air superiority shapes the sky.
Russian disinformation is affecting public perception of the Ukraine conflict, leading to a drop in America's support for Ukraine. Recognizable slogans and misinformation tactics are playing a pivotal role in shaping opinion.
With the advent of tweetable slogans such as “Hawaii not Ukraine” or “Let’s send another $10 Billion to Ukraine,” it can be surmised that Russian disinformation has has an effect on public perception of the war. Russian disinformation bots and sophists have still have the pedal to the floor, pumping out disinformation and it appears to be working. Americans are being tricked into supporting Russia’s interests.
Why a Strategy for Information War Matters
Imagine a scenario where the People’s Liberation Army of China starts to gear up for an invasion of Taiwan. While the nightly news reports the buildup, no pro-Taiwan information on the popular social media platform TikTok can be found. Instead, we see videos of people joking about nuclear war and the destruction of America. Memes on social media focus on nuclear war.
We have just let the adversary shape the battlespace.
The Current State of Offensive Information Warfare
The First Amendment to the US Constitution states:
Congress shall make no law respecting an establishment of religion, or prohibiting the free exercise thereof; or abridging the freedom of speech, or of the press; or the right of the people peaceably to assemble, and to petition the Government for a redress of grievances.
While the US has some pretty good Psychological Operations (PSYOPS) resources, they rightfully cannot be employed against Americans.

The US Navy provides Visual Information Personnel (VIPER) teams on some ships in the Pacific. These teams record People’s Liberation Army Navy ships that are performing dangerous maneuvers so that the true story of the encounter can be told.
The military also has Public Affairs Officers (PAOs) who escort the media and help them tell the military’s story. I’ve worked with these PAOs quite frequently in the past few years and not once has a PAO ever demanded that I tell a specific story to access military content for my YouTube Channel. The PAO doesn’t tell you what to publish, they just give you the access to the people you need to tell your story.
The Solution to the Information Warfare Problem
The solution to the Information Warfare problem is twofold:
America needs to create an Offensive PAO office.
America needs to considered targeting adversary information warfare capabilities.
The Offensive PAO
The Offensive PAO will be empowered to use available resources to work with content creators to tell the story of why we fight. This Offensive PAO will be empowered to work in internet time, giving content creators truthful and accurate information about the context of unfolding events.
Example:
From January 28 to February 4, 2023, a Chinese-owned high-altitude balloon traversed North American airspace, spanning Alaska, western Canada, and the contiguous United States. While there was significant media coverage of the event, the media and internet content creators were left to guess at the purpose of why the US was waiting to shoot the balloon down.
An Offensive PAO could have worked with the media and content creators to explain how the US was allowing the balloon to remain on its path because the signals intelligence gathered from the balloon was more valuable than the intelligence that China could gain from spying. While the intelligence community knew the importance of delaying kinetic action against the balloon, this information was not disseminated to the public.
Targeting Information Warfare Practitioners
If information warfare can be used to shape the battlefield, then the foreign practitioners of information warfare should be considered combatants and afforded the same considerations as soldiers on the battlefield. These assets or the infrastructure of these assets should be targeted through cyber or kinetic action.
The Logical Conclusion
In this evolving era of information warfare and cybersecurity, it's crucial to adapt our strategies to shape the battlespace in our favor. With proactive measures, such as an Offensive PAO office and targeted actions against Information Warfare practitioners, we can better defend our interests and secure our nation in this new era of warfare.
The slides for this presentation are below.